how can check handshake password length
Connect to an sftp server. Arch Linux up to date connected directly to gateway via ethernet cable.
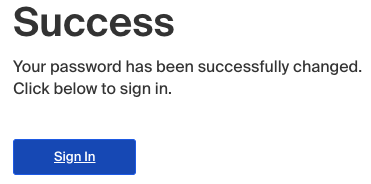
Reset The Password For A Student Account In Handshake Handshake Help Center
This limit can be overruled for specific services in the mastercf file.
. At the lowest level layered on top of some reliable transport protocol eg TCP is the TLS Record Protocol. A method is a byte sequence that matches the method token production. HTTPVERBSEC1 HTTPVERBSEC2 HTTPVERBSEC3 To normalize a method if it is a byte.
See postconf -d output The default Postfix SMTP server response template for a request that is rejected by an RBL-based restriction. Can anybody explain how I can solve this issue. That module is a general SSH2 client and server library and provides much more functionality than just SFTP connectivity.
This module is based on the excellent SSH2 module. It contains good options like the TCP options. Arch Linux up to date virtual machine on VirtualBox 4328r100309 Windows 81 host bridged network adapter.
Generate your own Password List or Best Word List There are various powerful tools. EAP-MsCHAP v2 can also be used as a standalone method for VPN but only as a PEAP inner method for wireless. Connectconfig SFTP object.
Password list download below best word list and most common passwords are super important when it comes to password cracking and recovery as well as the whole selection of actual leaked password databases you can get from leaks and hacks like Ashley Madison Sony and more. The TLS Record Protocol and the TLS Handshake Protocol. RFC 5246 TLS August 2008 1Introduction The primary goal of the TLS protocol is to provide privacy and data integrity between two communicating applications.
When you are capturing your data analyze the problem you will get the three-way handshake. EAP-Microsoft Challenge Handshake Authentication Protocol version 2 MS-CHAP v2 Secure password EAP-MS-CHAP v2 is an EAP type that can be used with PEAP for password-based network authentication. A forbidden method is a method that is a byte-case-insensitive match for CONNECT TRACE or TRACK.
From this you can determine the shift time and figure out if you have captured packets on the client-side or the server-side. The protocol is composed of two layers. A CORS-safelisted method is a method that is GET HEAD or POST.
This template can be overruled by specific entries in the optional rbl_reply_maps lookup table. Full documentation for connection options is available here.
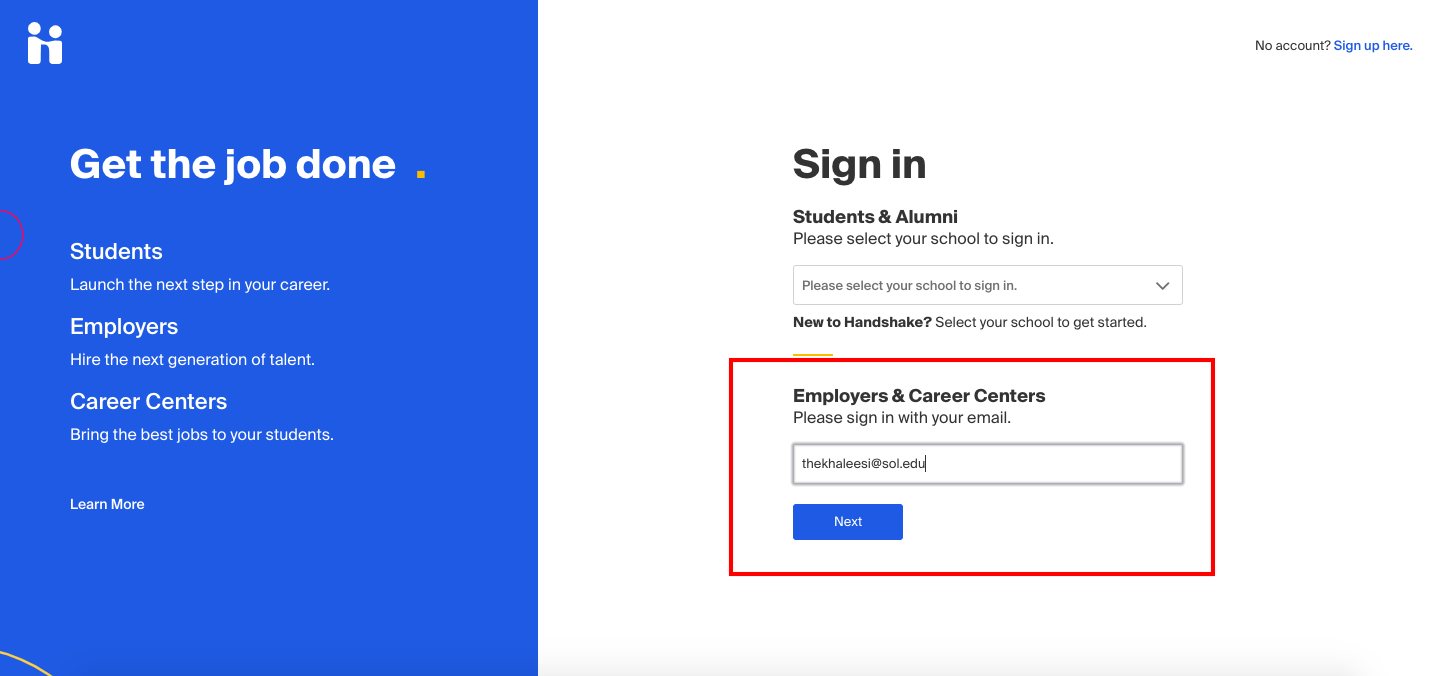
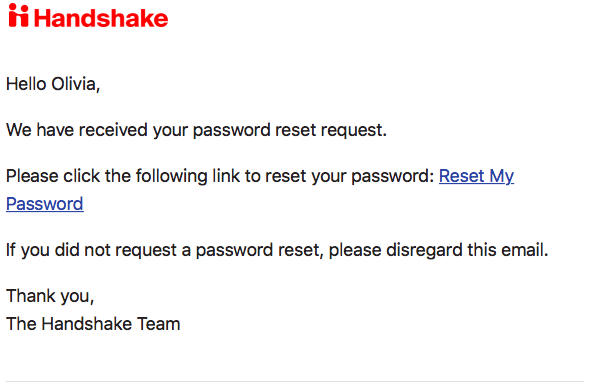
Log In As An Alum Set Your Handshake Password Handshake Help Center
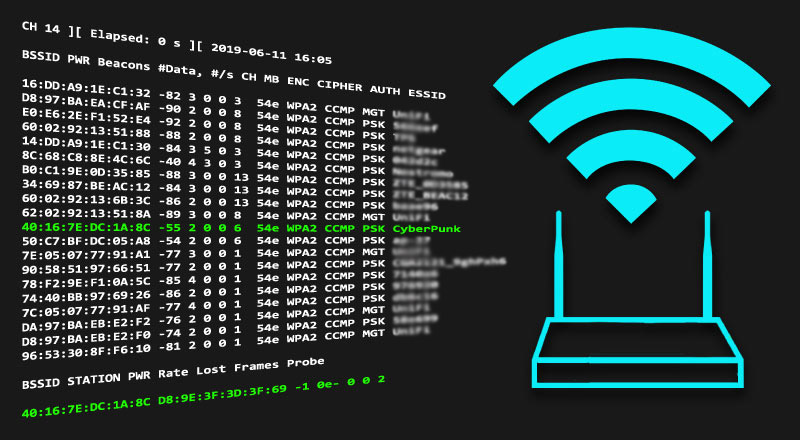
Capturing Wpa Wpa2 Handshake Cracking Principles Cyberpunk
Log In As An Alum Set Your Handshake Password Handshake Help Center
A Detailed Diagram Of The Four Way Handshake Msg Message Download Scientific Diagram

Reset The Password For A Student Account In Handshake Handshake Help Center
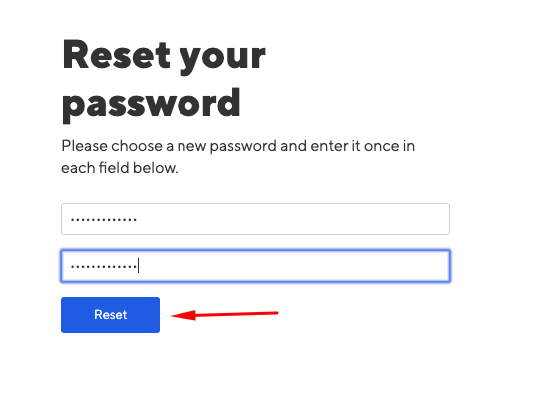
Reset Password For An Employer Account Handshake Help Center

Capture A Wireless Handshake How To Find A Wifi Password Packet Youtube
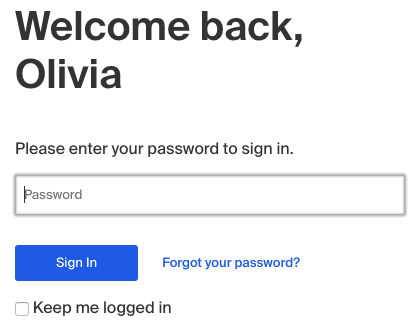
Reset The Password For A Student Account In Handshake Handshake Help Center
0 Response to "how can check handshake password length"
Post a Comment